Dual Authentication Patterns for Carrier Integration Middleware: Supporting SOAP and OAuth 2.0 During the 2026 Migration Wave
The 2026 carrier API migration wave is creating authentication chaos for multi-tenant carrier integration middleware. FedEx's final SOAP retirement deadline hits March 31, 2026, after which shipping with legacy web services ends worldwide. Meanwhile, USPS Web Tools APIs shut down on January 25, 2026. UPS already completed their OAuth transition in 2024, leaving platforms to support three distinct authentication patterns simultaneously during this transition.
For platform engineers building carrier integration middleware like Cargoson, nShift, or ShipEngine, this creates a complex architectural challenge: maintaining tenant isolation while supporting both legacy SOAP credentials and modern OAuth 2.0 flows. You can't simply flip a switch - different tenants migrate at different speeds, and some carriers require parallel authentication support during transition periods.
The Authentication Bridge Pattern
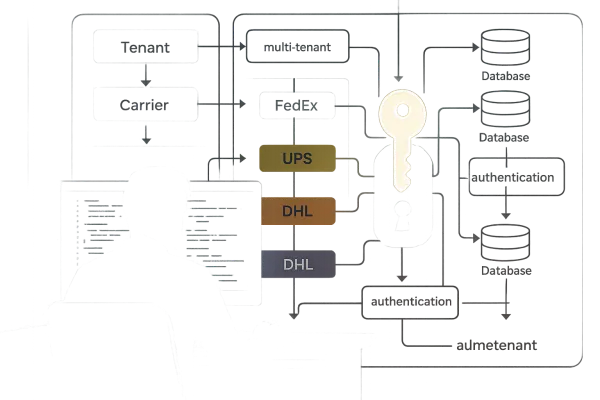
The core solution is an authentication bridge that routes requests based on per-tenant configuration and carrier compatibility. This pattern isolates credential management while providing fallback capabilities when authentication methods fail.
{
"tenant_id": "acme-corp",
"carrier_configs": {
"fedex": {
"auth_method": "soap_legacy",
"credentials": {
"api_key": "...",
"password": "...",
"account_number": "..."
},
"fallback_enabled": false
},
"usps": {
"auth_method": "oauth2_rest",
"credentials": {
"client_id": "...",
"client_secret": "...",
"refresh_token": "..."
},
"soap_fallback": {
"enabled": true,
"credentials": {...}
}
}
}
}The authentication bridge sits between your application layer and carrier adapters. When processing a shipment request, it queries the tenant's authentication configuration and routes to the appropriate credential handler. FedEx APIs offer improved security through OAuth token-based authentication, but the bridge must simultaneously support legacy SOAP for tenants not yet migrated.
Circuit breaker patterns become essential here. If OAuth authentication fails, the bridge can automatically fall back to SOAP credentials where configured. This prevents service disruptions during the migration window while maintaining proper audit trails for each authentication attempt.
SOAP Legacy Credential Management
Legacy SOAP credentials require different storage and security patterns than modern OAuth tokens. SOAP typically uses long-lived API keys combined with XML signature authentication, stored in tenant-scoped credential vaults.
The key difference is lifecycle management. SOAP credentials are static - once configured, they remain valid until manually rotated. This means your credential storage must support versioning for gradual rollouts and emergency rollbacks.
// Tenant credential isolation pattern
class TenantCredentialVault {
async getSoapCredentials(tenantId, carrier) {
const credentials = await this.decrypt(
this.storage.getCredentials(tenantId, carrier, 'soap')
);
// Validate credential freshness
if (this.isExpiringSoon(credentials.created_at)) {
this.scheduleRotation(tenantId, carrier);
}
return credentials;
}
}Migration flags per tenant allow gradual rollouts. Set a tenant to "dual_auth" mode, and the system attempts OAuth first, falling back to SOAP on failure. This gives you confidence that the OAuth integration works before disabling SOAP entirely.
OAuth 2.0 Implementation Patterns
OAuth 2.0 for carrier integration typically uses the client credentials flow for server-to-server communication. USPS Version 3 uses OAuth 2.0 for API authentication, replacing legacy authentication methods and requiring generation and management of new tokens.
Token lifecycle management becomes more complex in multi-tenant environments. Each tenant needs isolated token storage, with automatic refresh logic that doesn't interfere with other tenants' authentication flows.
class OAuthTokenManager {
async getValidToken(tenantId, carrier) {
let token = await this.getToken(tenantId, carrier);
if (this.isExpiring(token)) {
token = await this.refreshToken(tenantId, carrier);
}
return token;
}
async refreshToken(tenantId, carrier) {
const lock = await this.acquireLock(`${tenantId}:${carrier}`);
try {
// Double-check pattern to avoid race conditions
const currentToken = await this.getToken(tenantId, carrier);
if (!this.isExpiring(currentToken)) {
return currentToken;
}
const newToken = await this.performTokenRefresh(tenantId, carrier);
await this.storeToken(tenantId, carrier, newToken);
return newToken;
} finally {
await lock.release();
}
}
}Webhook signature verification adds another layer. Many OAuth-enabled carrier APIs now include HMAC signatures in webhook payloads. Your middleware must validate these signatures using tenant-specific secrets, preventing cross-tenant webhook spoofing attacks.
Transition State Management
Managing dual authentication modes requires careful state tracking per tenant. The challenge is supporting "OAuth-preferred with SOAP fallback" while maintaining audit trails and performance metrics for both authentication paths.
Per-tenant migration status tracking lets you monitor rollout progress. Track metrics like OAuth success rate, fallback frequency, and authentication latency for each tenant-carrier combination. This data drives migration decisions and identifies problematic integrations early.
// Migration state machine per tenant
const migrationStates = {
SOAP_ONLY: 'soap_only',
DUAL_AUTH: 'dual_auth', // OAuth preferred, SOAP fallback
OAUTH_ONLY: 'oauth_only',
TESTING: 'testing' // OAuth enabled for validation calls only
};Testing patterns become crucial during migration. Implement "shadow mode" where OAuth requests run in parallel with SOAP requests, comparing responses without affecting production traffic. This validates OAuth integration correctness before switching over.
Monitoring and alerting must distinguish between authentication methods. Set up separate error thresholds for OAuth vs SOAP failures. A spike in OAuth failures might indicate carrier API issues, while SOAP failures during migration could mean credential configuration problems.
Security Implications and Tenant Isolation
Dual authentication increases the attack surface for credential leakage between tenants. OAuth tokens are shorter-lived but more complex to manage. SOAP credentials are simpler but longer-lived and more dangerous if compromised.
Credential storage encryption must support multiple key types. OAuth client secrets, refresh tokens, and access tokens each have different security requirements. SOAP API keys often need backwards compatibility with legacy encryption schemes.
Audit logging becomes more complex with dual authentication. Each authentication attempt - whether OAuth or SOAP - must log the tenant, carrier, authentication method, success/failure, and any fallback actions taken. This audit trail is essential for security incident response and compliance.
// Enhanced audit logging for dual auth
await auditLogger.log({
tenant_id: 'acme-corp',
carrier: 'fedex',
auth_method_attempted: 'oauth2',
auth_result: 'failed',
fallback_method: 'soap',
fallback_result: 'success',
request_id: 'req_123',
timestamp: '2026-02-11T10:30:00Z',
failure_reason: 'token_expired'
});Key rotation strategies must account for migration timing. You can't rotate SOAP credentials while they're acting as fallbacks for failed OAuth attempts. Coordinate credential rotation with migration status to avoid authentication outages.
Production Migration Strategies
Phased rollouts by tenant risk profile work better than carrier-by-carrier migrations. Start with low-volume tenants or those with flexible SLAs. High-volume shippers with strict uptime requirements migrate last, after you've validated the OAuth integration thoroughly.
Rollback procedures become more complex with dual authentication. If OAuth fails during production migration, you need instant fallback to SOAP without manual intervention. Build automated rollback triggers based on authentication failure rates or API error thresholds.
Performance monitoring must track both authentication methods separately. OAuth typically adds latency due to token refresh operations, while SOAP has consistent performance but higher payload overhead. REST APIs offer smaller response payloads, improving integration performance compared to SOAP.
The migration timeline requires coordination with carrier deprecation schedules. FedEx's remaining SOAP endpoints retire in June 2026, after which integrations must use REST APIs. Plan tenant migrations to complete well before these hard deadlines.
Integration monitoring platforms like DataDog or New Relic need separate dashboards for OAuth and SOAP metrics. Track token refresh frequencies, authentication latencies, and fallback activation rates. These metrics help identify optimal migration timing for each tenant.
The authentication bridge pattern provides a robust foundation for managing the 2026 carrier migration wave. By isolating credential management, supporting gradual rollouts, and maintaining comprehensive audit trails, you can navigate this complex transition while preserving tenant isolation and service reliability. The key is treating authentication method as a per-tenant configuration decision rather than a platform-wide switch.