Multi-Tenant API Versioning for Carrier Integration: Preventing Cascade Failures When Breaking Changes Hit Hundreds of Shippers

Your traditional API versioning just became exponentially more dangerous. When a breaking change hits your single-tenant middleware, you fix one system. When it hits multi-tenant carrier integration middleware serving 500 shippers, you've got 500 potential failures cascading through your platform simultaneously.
Most carrier integration platforms serve multiple shippers. Your monitoring architecture must isolate performance data and alerting per tenant while efficiently sharing carrier connections. The challenge isn't just managing version transitions anymore. You're orchestrating hundreds of independent upgrade schedules while preventing one tenant's integration problems from breaking everyone else's shipping operations.
The Multi-Tenant API Versioning Crisis in Carrier Integration
Traditional API versioning strategies collapse under multi-tenant constraints. Research indicates that APIs with clear versioning experience 40% fewer security issues during transitions, making proper versioning strategies a crucial component of robust API architecture. But that research assumes single-tenant deployments where you control the upgrade timeline.
In carrier integration middleware, a single API version change affects every tenant simultaneously. When FedEx updates their rate shopping endpoint or UPS modifies their tracking response schema, you can't just push the change and hope your clients adapt. According to recent surveys: 67% of developers have experienced unexpected API breaking changes · Average downtime cost: $5,600 per minute for enterprise applications.
Now multiply that $5,600 by the number of tenants hitting the same breaking change. A platform like Cargoson or competitors like nShift, EasyPost, or ShipEngine must isolate version impacts per tenant while maintaining shared infrastructure efficiency. This lack of versioning eliminates your control over the upgrade cadence, forcing you to adapt to potentially breaking changes, unexpected UI shifts, or deprecated functionality reactively rather than proactively.
The economics are brutal. This approach has saved us approximately $47,000 in potential downtime costs and countless hours of debugging. But that's for a single application. When you're managing hundreds of tenants, each with different risk tolerances and upgrade capabilities, the cost of getting versioning wrong scales linearly with your tenant count.
Understanding Tenant Boundary Violations During API Updates
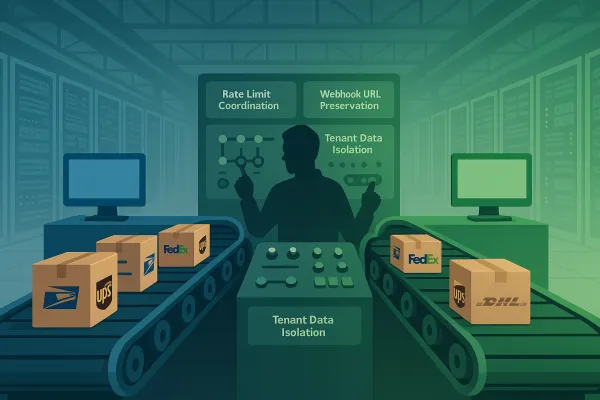
Multi-tenant API versioning introduces a class of failures that don't exist in single-tenant systems: cross-tenant contamination during version transitions. Multi-tenant architecture's main point is data isolation, so it has to be carefully maintained and sought. It's imperative to ensure that tenants do not have access to each other's private data.
Consider this scenario: You're rolling out FedEx API v3.2 which changes the webhook payload format. Tenant A upgrades successfully, but their new webhook handler starts processing webhook deliveries intended for Tenant B who's still on v3.1. The routing logic assumes all tenants are on the same version, creating a data breach disguised as a versioning problem.
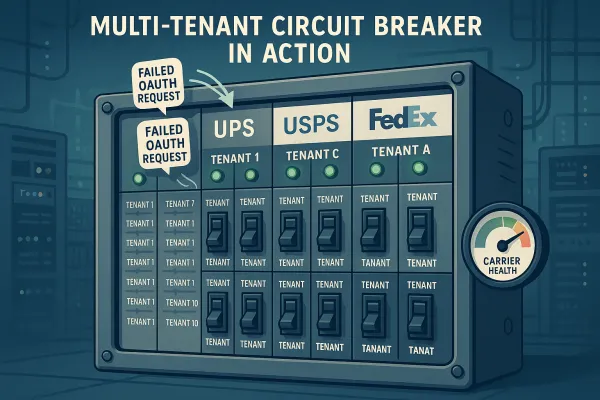
The global rate limiter failed to distinguish between tenants, allowing one company's malfunctioning integration to consume 70% of the API throughput. Meanwhile, background workers pulled jobs from a single FIFO (first in, first out) queue, causing a tenant with millions of assets to block smaller tenants entirely. This cascades during version updates when one tenant's broken integration on the old API version consumes resources needed for tenants upgrading to the new version.
Authorization logic becomes particularly fragile during multi-tenant API transitions. The first line of defense sits at the edge — load balancers, API gateways, and reverse proxies that enforce tenant routing before requests ever reach your application. A misconfigured gateway won't stop authenticated users from crossing tenant boundaries, but it prevents basic manipulation attempts and creates an audit trail.
The Economics of Breaking Changes at Scale
Integration bugs cost individual organizations $8.2 million annually, but for multi-tenant platforms, the math is different. You're not just losing one customer's revenue during an outage. You're potentially losing hundreds of customers simultaneously, each with their own SLAs and contract penalties.
Major TMS providers like MercuryGate, Descartes, and Cargoson must calculate downtime costs across their entire tenant base. If your platform serves 300 enterprise shippers and experiences a breaking change that affects 60% of them, you're looking at 180 separate incident timelines, each with different escalation procedures and financial impact calculations.
For businesses operating in heavily regulated industries, the financial impact of a data breach can be severe - costs may rise by 58% in the first year alone. When a versioning error causes cross-tenant data exposure in carrier integration middleware, you're not just dealing with technical downtime. You're facing potential regulatory violations across multiple industries and jurisdictions.
Versioning Strategies That Preserve Tenant Isolation
Effective multi-tenant API versioning requires tenant-aware routing at every layer. API versioning is the practice of managing changes to an API and assigning unique identifiers to different iterations. It allows API producers to introduce new features, fix bugs, or alter data structures while allowing consumers to continue using a stable, predictable version until they are ready to migrate. This process is fundamental to maintaining a healthy relationship between an API provider and its consumers.
But in multi-tenant environments, that "readiness to migrate" varies dramatically across tenants. Here's the architecture that works:
Header-Based Versioning with Tenant Context: This approach is particularly useful for APIs in industries like finance or healthcare, where frequent updates and strict backward compatibility are critical. By using semantic versioning (e.g., major.minor.patch) within headers, teams can effectively manage complex version hierarchies while maintaining a clean and secure interface.
X-API-Version: 2.1.0
X-Tenant-ID: shipper_12345
X-Tenant-Version-Lock: v2.1.0
This allows tenant-specific version pinning while sharing the same infrastructure. The gateway routes based on both tenant and version, preventing cross-tenant contamination.
Circuit Breakers Per Tenant-Version Combination: A circuit breaker prevents your system from hammering a failing API continuously. If failures exceed a threshold, the circuit opens and blocks calls temporarily. In multi-tenant environments, you need circuit breakers that understand tenant boundaries. A failing integration for one tenant shouldn't trigger circuit breaker protection for other tenants on the same API version.
Semantic Versioning in Multi-Tenant Context
SemVer suggests versioning in the format of MAJOR.MINOR.PATCH, providing a standardized approach to version numbering. For multi-tenant carrier middleware, extend semantic versioning with tenant-specific metadata:
- MAJOR: Breaking changes that require tenant opt-in
- MINOR: New features with backward compatibility across all tenants
- PATCH: Bug fixes that can be automatically applied
- Tenant Extension: +tenant.shipper_12345.locked indicates version lock status
This creates an audit trail for every tenant's version status and enables automated compatibility checking. Platforms like Cargoson use this alongside competitors to ensure version transitions don't break tenant isolation.
Implementation Patterns: From Theory to Production
Other systems rely on tenant identifiers stored in authentication tokens or session data. API-first SaaS platforms often embed tenant identifiers into API keys or JWT claims. For carrier integration, this becomes more complex because you're proxying between tenant requests and carrier APIs while maintaining version compatibility.
Here's a production-ready tenant-aware versioning implementation:
async function routeCarrierRequest(request) {
const { tenantId, apiVersion } = extractTenantContext(request);
const tenantConfig = await getTenantVersionConfig(tenantId);
// Validate version compatibility
if (!isVersionCompatible(apiVersion, tenantConfig.lockedVersion)) {
throw new VersionMismatchError(tenantId, apiVersion);
}
// Route to version-specific handler
const handler = getVersionHandler(apiVersion);
const circuitBreaker = getTenantCircuitBreaker(tenantId, apiVersion);
return circuitBreaker.execute(() => handler(request));
}
Implementing an API gateway provides a centralized point for handling versioning: Benefits: Centralizes routing logic, can apply version-specific transformations. Implementation: Use tools like Kong, AWS API Gateway, or a custom Node.js/Express gateway.
Performance considerations become critical at scale. Budget for increased testing requirements across all supported versions. Plan for additional server resources if multiple versions have different performance characteristics. Allocate developer time for maintaining backward compatibility.
Breaking Change Detection and Communication
Changelogs and Release Notes: Publish a detailed changelog with every update, clearly distinguishing between major (breaking), minor (feature), and patch (bug fix) changes. Using Semantic Versioning (SemVer) is a highly recommended standard for this. Proactive Notifications: Use multiple channels, such as email newsletters, blog posts, and status pages, to inform consumers about upcoming versions, changes, and deprecation schedules.
For multi-tenant platforms, communication must be tenant-aware. Not every tenant needs to know about every change. A pharmaceutical shipper doesn't need alerts about automotive-specific label format updates. Segment your communications by tenant industry, integration complexity, and risk profile.
Automated testing across tenant versions requires sophisticated test matrices. After getting burned too many times, we built a proactive change detection system that monitors not just availability, but behavior consistency. Your test suite must validate not just that each version works, but that version transitions don't create cross-tenant issues.
Operational Considerations: Monitoring and Rollback
Implement shared libraries for common functionality across versions. Automate testing for all versions to quickly identify regressions. Document version-specific behaviors to aid troubleshooting. But shared libraries introduce their own multi-tenant risks. A change to shared code can affect multiple versions and tenants simultaneously.
SLO monitoring must be tenant and version-aware. If your monthly error budget allows 100 failed requests, but 50 failures happen in the first week, you're burning budget too quickly. Alert on these trends before you exhaust your error budget and breach customer SLAs.
Structure your observability for multi-dimensional analysis:
api_request_duration{
tenant_id="shipper_12345",
api_version="v2.1.0",
carrier="fedex",
endpoint="rate_shopping"
}
Use consistent field naming across carriers - normalize UPS's "ResponseTime" and FedEx's "ProcessingDuration" into a standard "api_duration_ms" field. This consistency enables cross-carrier performance comparisons and simplifies alerting logic.
Rollback procedures in multi-tenant environments require surgical precision. You can't just roll back the entire platform when one tenant's version upgrade fails. Build rollback capabilities that operate at the tenant level while preserving isolation boundaries.
Cost and Capacity Planning
Caching plays a major role in improving the speed and responsiveness of multi-tenant SaaS apps. Because multiple tenants access the same resources, efficient caching prevents your system from reprocessing identical queries repeatedly. Technologies like Redis, Memcached, edge caching, and CDN caching can dramatically reduce server load.
Version maintenance costs compound in multi-tenant environments. Each supported version requires:
- Dedicated test suites (multiply by tenant count for isolation testing)
- Version-specific monitoring and alerting infrastructure
- Customer support training for version-specific behaviors
- Security patching across all supported versions
Calculate version sunset economics carefully. While this works well for smaller or fast-changing APIs, managing numerous versions over time can become a headache. To keep things organized, teams should establish clear deprecation policies and communicate changes effectively.
Future-Proofing Your Versioning Architecture
A thoughtful API versioning strategy has a profound, positive impact on the entire software ecosystem. It promotes stability, allowing client applications to operate without fear of sudden failures due to unannounced API updates. This reliability builds trust and encourages wider adoption of the API. For the provider, it facilitates innovation by creating a safe framework for releasing improvements and new functionalities. In a microservices-based architecture, clear versioning is the glue that holds the system together, enabling independent service evolution without causing a cascade of failures across the network.
The future of multi-tenant API versioning lies in treating versions as first-class tenant resources. Instead of versioning APIs, version tenant capabilities. Allow tenants to opt into new features gradually while maintaining strict isolation boundaries.
Consider date-based versioning for rapidly evolving carrier integrations. When FedEx ships weekly updates and UPS follows quarterly cycles, semantic versioning can't keep pace. Date-based versions (2025-01-14, 2025-01-21) provide clear chronological ordering while allowing tenant-specific adoption schedules.
AI integration adds new complexity. AI agents introduce something new: super-users with no judgment. An LLM processing data across tenants doesn't "know" which tenant a record belongs to. It sees text, generates responses, and follows instructions — sometimes instructions embedded in user data. Version your AI model deployments with the same tenant isolation principles.
Regulatory changes will drive versioning requirements. GDPR updates, industry-specific compliance changes, and regional shipping regulations create mandatory version upgrades for affected tenants. Build your versioning architecture to handle compliance-driven updates that can't be delayed or rolled back.
The platforms that survive will treat multi-tenant API versioning as a core competency, not an afterthought. Start designing for tenant isolation from day one, because retrofitting version boundaries into a running multi-tenant system is exponentially harder than building them correctly from the start.