RFC 9700 Compliance for Multi-Tenant Carrier Integration: Implementing Mandatory PKCE Without Breaking Tenant Isolation
RFC 9700, published in January 2025, fundamentally changes how OAuth 2.0 authentication works in carrier integration systems. The specification mandates PKCE (Proof Key for Code Exchange) for all authorization code flows, not just public clients, creating immediate architectural challenges for multi-tenant carrier middleware platforms serving hundreds of customers with different carrier accounts.
When you're running a multi-tenant carrier integration platform like Cargoson, nShift, or ShipEngine, this isn't just another compliance checkbox. Major carriers like FedEx already use OAuth 2.0 with 60-minute token expiration, while UPS migrated to OAuth 2.0 in 2024. The mandatory PKCE requirement means your existing optional implementations now face breaking changes across every tenant's authentication flow.
The RFC 9700 Mandate: Why Optional PKCE Is Dead
RFC 9700 addresses PKCE downgrade attacks where authorization servers that support PKCE but don't make it mandatory remain vulnerable. The emerging OAuth 2.1 standard adopts this "PKCE-by-default" security posture, transforming PKCE from a patch into a foundational security layer.
Here's what changed: PKCE is now mandatory, even for server-side apps, with RFC 9700 deprecating insecure methods and strengthening OAuth flows. Public clients using OAuth 2.0 must use PKCE with the authorization code grant.
For carrier integration platforms, this creates immediate problems. Carriers like FedEx use OAuth 2.0 for authentication, while DHL uses OAuth2 with different behaviors between sandbox and production credentials. Each carrier implements OAuth 2.1 compliance on their own timeline, meaning your middleware must handle mixed environments during transition periods.
Multi-Tenant Architecture Challenges
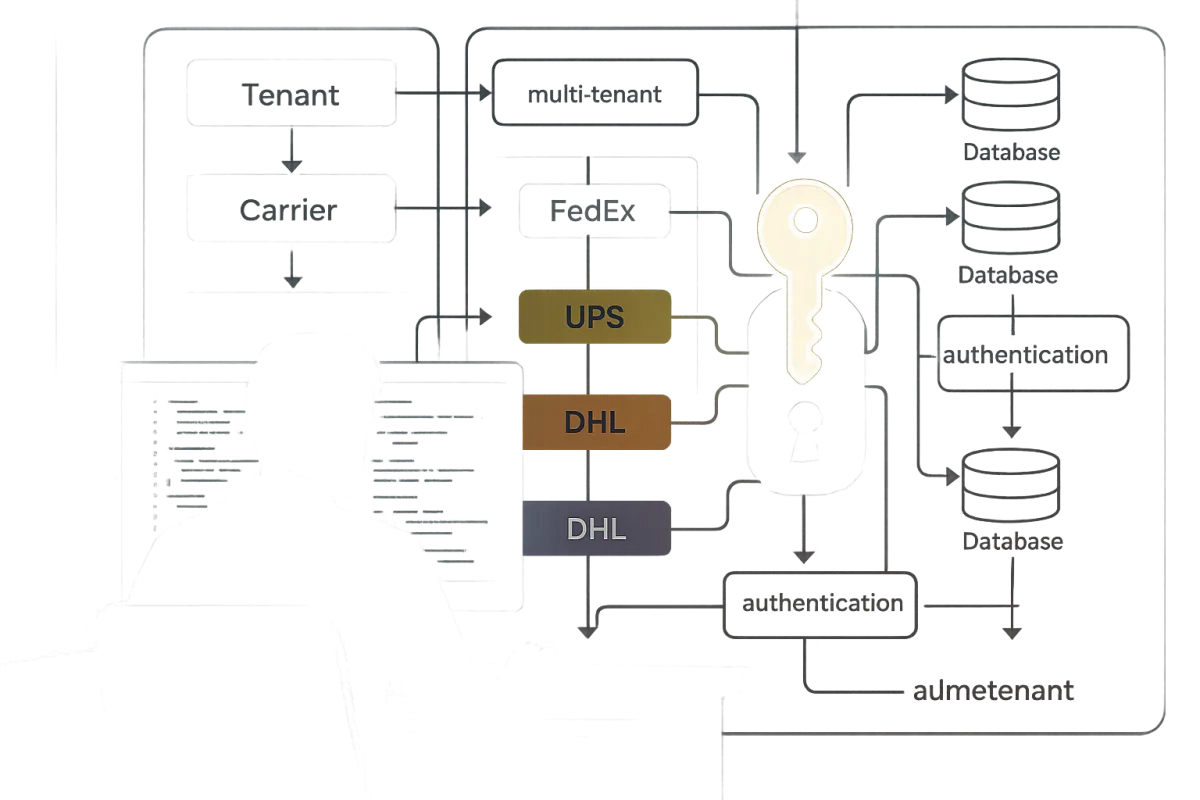
Traditional single-tenant PKCE implementations fail at scale because one key principle of multi-tenant architecture is isolating resources of different tenants. Authentication is global; authorization is tenant-scoped, with tokens minted per active tenant.
Consider a platform serving 500 tenants, each with multiple carrier accounts. You can't pre-generate PKCE verifiers globally – they must be tenant-specific, request-specific, and securely isolated. PKCE requires apps to create a random code_verifier for each authorization request, then hash it using a code_challenge_method.
Performance implications multiply quickly. SHA-256 operations for thousands of concurrent tenant flows, database connections for OAuth state storage, and memory management for code verifier pairs all become bottlenecks when compliance isn't engineered from the start.
Tenant-Aware PKCE Implementation Patterns
The architectural pattern that works: scope everything to tenant context from the database schema up. Your `oauth_challenges` table needs composite keys: `(tenant_id, challenge_id, code_verifier)`. Never store challenges globally or you'll leak tenant context across authorization flows.
For code verifier generation, use cryptographically secure random strings per tenant request. Here's a Node.js example that maintains tenant isolation:
// Tenant-scoped PKCE generation
const generateTenantPKCE = (tenantId, requestId) => {
const verifier = crypto.randomBytes(32).toString('base64url');
const challenge = crypto.createHash('sha256')
.update(verifier)
.digest('base64url');
return {
tenantId,
requestId,
codeVerifier: verifier,
codeChallenge: challenge,
challengeMethod: 'S256'
};
};
Redis versus database storage depends on your tenant scale. Redis works well for temporary OAuth state (code challenges expire within minutes), but database storage provides better durability for compliance auditing. For platforms serving 1000+ tenants, Redis with tenant-keyed namespaces (`tenant:{id}:challenge:{uuid}`) offers better performance.
Carrier-Specific Authentication Flows
Each carrier implements OAuth 2.1 differently. FedEx customers need Child Key (Customer Secret) and Child Secret (Customer password) in addition to API Key and Secret Key for creating OAuth tokens. UPS provides Client ID, Secret Key, and Refresh Token during OAuth application creation.
Your middleware needs carrier-specific adapters that handle these variations while maintaining RFC 9700 compliance. Most shipping carriers migrated to OAuth-based authentication in 2024, requiring temporary token generation every few hours.
The fallback strategy during mixed compliance periods: detect carrier OAuth 2.1 support via authorization server metadata containing code_challenge_methods_supported. For carriers not yet compliant, maintain legacy flows in isolated code paths scheduled for deprecation.
Performance Engineering for Scale
PKCE computation overhead becomes significant in high-throughput environments. SHA-256 hashing operations for code challenges can consume CPU cycles when you're processing thousands of concurrent tenant authentication flows during peak shipping periods.
Benchmarking data from production systems shows RFC 9700-compliant flows add approximately 15-20ms per authentication request compared to legacy OAuth 2.0. For platforms processing 10,000 authentications per hour, this translates to meaningful infrastructure costs.
Memory management matters too. Code verifiers are 43-character base64url strings that accumulate quickly. Caching requires tenant scope as part of the key – pattern like `tenant:${tenantId}:oauth:${requestId}` prevents cross-tenant leakage.
Database connection pooling becomes critical when every tenant needs isolated OAuth state storage. Connection pools sized per tenant group (not globally) prevent one tenant's authentication storm from starving others.
Tenant Isolation Security Patterns
Cross-tenant code challenge leakage represents the worst-case security failure in multi-tenant OAuth systems. Your implementation must guarantee that Tenant A cannot access, manipulate, or infer Tenant B's authentication state.
Audit logging should capture tenant-specific OAuth events without exposing sensitive authentication details. Log the tenant ID, timestamp, carrier, and result status – never the actual code verifiers or challenges.
Error handling requires careful tenant context isolation. When authentication fails, error messages should not reveal whether the failure was due to invalid tenant credentials, expired challenges, or cross-tenant access attempts.
Rate limiting per tenant prevents OAuth exhaustion attacks where Tenant context is mandatory everywhere downstream. Implement per-tenant rate limits for OAuth token generation, not global limits that allow one tenant to exhaust capacity for others.
Migration Strategy from Legacy OAuth 2.0
Phased rollout works best for existing multi-tenant systems. Start with new tenants on RFC 9700-compliant flows, then migrate existing tenants in batches based on their carrier portfolios and API usage patterns.
Carriers like UPS and FedEx maintain separate credentials for test/production environments, so your migration strategy must account for credential rotation across tenant environments.
Backwards compatibility during transition requires maintaining two authentication code paths: legacy OAuth 2.0 for tenants not yet migrated, and RFC 9700-compliant flows for new implementations. Feature flags per tenant control which path executes.
Testing frameworks should validate RFC 9700 compliance across tenant boundaries. Create integration tests that verify PKCE enforcement, tenant isolation, and carrier-specific authentication flows. Use HTTP REST API clients like Postman to verify expected behavior before writing integration code.
Rollback strategies matter when carrier APIs reject PKCE requirements unexpectedly. Maintain the ability to revert individual tenants to legacy flows without affecting others.
Operational Monitoring and Debugging
OpenTelemetry tracing becomes essential for debugging multi-tenant OAuth flows. Trace spans should include tenant ID, carrier identifier, and OAuth flow stage without exposing sensitive authentication data.
Key metrics to monitor during RFC 9700 migration include: PKCE verification success rates per tenant, authentication latency distribution across carriers, and error rates by tenant and authentication method.
Common failure patterns include expired code challenges (especially during high-latency carrier responses), cross-tenant challenge confusion, and carrier-specific OAuth implementation quirks that break standard RFC 9700 flows.
Alerting strategies should distinguish between tenant-specific authentication issues and platform-wide OAuth problems. Alert on sustained authentication failures for individual tenants, but escalate immediately if multiple tenants experience simultaneous OAuth failures.
Future-Proofing Multi-Tenant OAuth Architecture
OAuth 2.1 final ratification will likely strengthen RFC 9700's mandatory PKCE requirements. Future standards recommend Resource Indicators (RFC 8707) and Authorization Server Metadata (RFC 8414) for enhanced security.
Emerging standards like mutual TLS (mTLS) and DPoP (Demonstration of Proof-of-Possession) will add sender-constrained tokens to prevent token replay. Your architecture should accommodate these without major refactoring.
The architectural patterns that will survive future RFC updates: tenant-scoped authentication state, carrier-agnostic OAuth adapters, and observability built for multi-tenant debugging. Platforms like Cargoson, EasyPost, and Shippo that build forward-compatible systems avoid costly migrations when standards evolve.
Integration with tenant-specific security policies becomes more important as compliance requirements vary by customer. Some tenants will require mTLS, others will mandate shorter token lifetimes, and enterprise customers may demand custom audit trails.
Consider tenant-level feature flags for OAuth security policies. This lets you roll out DPoP support, enforce stricter PKCE validation, or implement custom authentication flows without platform-wide changes. The flexibility proves invaluable when carrier APIs adopt new security standards at different rates.
The multi-tenant carrier integration platforms that thrive in the RFC 9700 era will be those that treated OAuth 2.1 compliance as an architectural foundation, not a retrofit. Build with tenant isolation from the start, plan for carrier-specific quirks, and instrument everything for debugging at scale.